About Me
@thejolotoproject is a passionate sole developer who builds modern web and mobile applications using up-to-date programming languages, frameworks, and best practices.
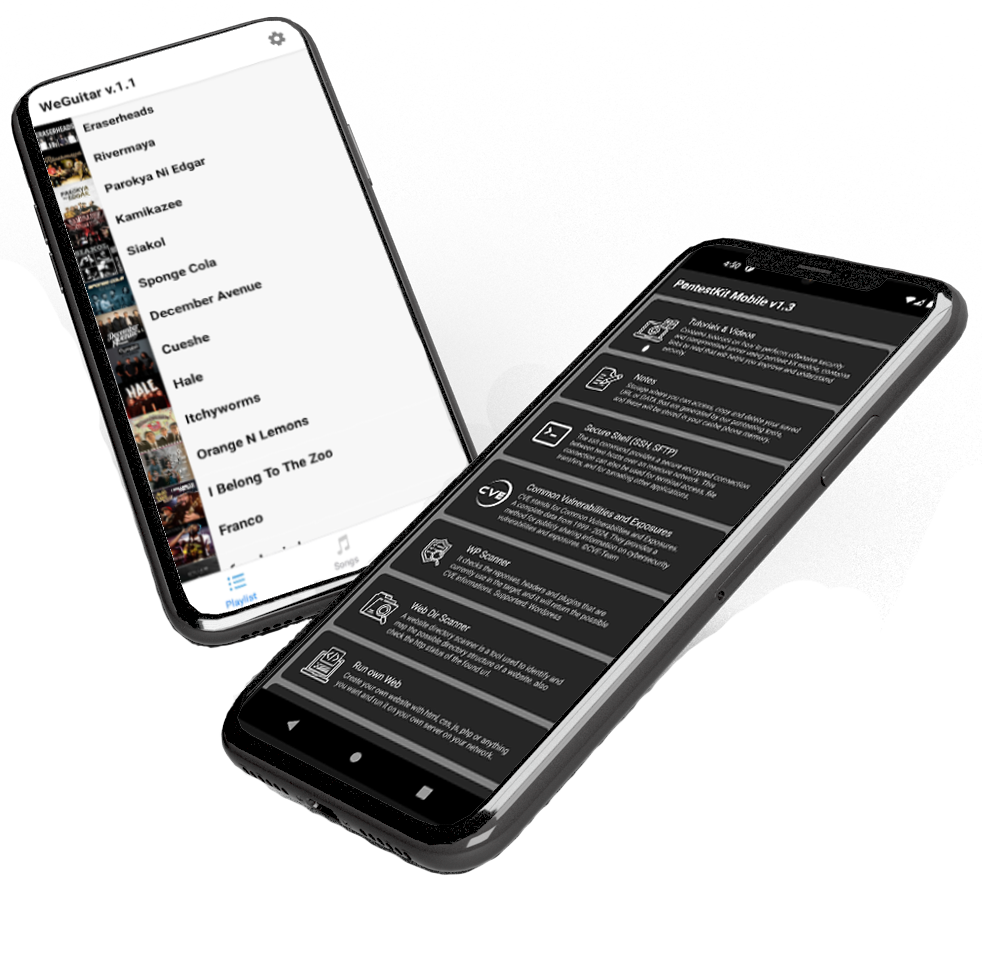
@thejolotoproject is the personal brand of John Lodan Tojot, a developer behind the mobile apps Weguitar and PentestKit Mobile. Weguitar includes over 700 OPM songs with lyrics and chords. PentestKit is a mobile cybersecurity toolkit for security enthusiasts and penetration testers, featuring built-in reconnaissance and post-exploitation tools to support real-world security research.
My journey into Cybersecurity began in 2012. I dove into Penetration Testing, exploring system and application vulnerabilities, and actively participated in various events such as Capture The Flag (CTF), SQLi/XSS challenges, and Cyberwar simulations. Offensive Security quickly became my favorite focus area. Back in the day, I used Backtrack 5 before Kali Linux 1.0 was even released. Good old times! I set up numerous security labs on my local machine, experimented with scripts (including my own), and hunted for 0-day exploits on Exploit-DB to test them safely in controlled environments. That’s where my obsession with cybersecurity took root, and it never left.
In 2017, I transitioned into Software Engineering, where I began building full systems and applications from the ground up. My work spans planning architecture, converting UI designs into responsive web pages, building APIs, processing data, and managing database integration, covering both frontend and backend development. Over time, I expanded into DevOps, handling server and domain setups and deployments, a role I’ve carried through to the present day (2025).
Outside of tech, I’m deeply into music. I enjoy playing various instruments like guitar, bass, drums, and keyboards. I especially love listening to classics from the ‘90s. And of course, you can’t beat some good old OPM (Original Pilipino Music)!
Blogs & Tutorials
Learn about cybersecurity concepts through educational tutorials that promote responsible and legal security testing. Tutorials use tools like PentestKit Mobile to help developers and security enthusiasts understand system vulnerabilities and how to strengthen them. As a software developer, understanding how attackers think enables you to build more secure applications and defend against real-world threats.

What is Pentestkit Mobile? – Your All-in-One Toolkit for Mobile Penetration Testing?
A mobile toolkit for security enthusiasts — scan, exploit, and manage compromised servers all from your phone.
For educational purposes only. Reading this will help you understand how attackers think and how to defend your website and server.

How to Perform Local File Inclusion (LFI), Achieve Remote Code Execution (RCE), and Root a Server Using Pentestkit Mobile.
[W/ Youtube Video] A step-by-step guide to exploiting LFI, escalating to RCE, and rooting a server using PentestKit Mobile.
For educational purposes only. Reading this will help you understand how attackers think and how to defend your website and server.

How to Perform Offensive Security & Compromised a Web Server using PentestKit Mobile
[W/ Youtube Video] See how to used PentestKit Mobile to scan, exploit, and gain persistent access to a vulnerable web server.
For educational purposes only. Reading this will help you understand how attackers think and how to defend your website and server.

Understanding Time-Based Blind RCE: Exploiting Without Seeing Output.
Learn how attackers exploit servers using time-based blind RCE when no output is visible.
For educational purposes only. Reading this will help you understand how attackers think and how to defend your website and server.


